QUIZ QUESTIONS ON COMPUTERS
Welcome to our interactive "Quiz on Computers"! This is a 50- question quiz to test your computer-related knowledge? Whether you're a tech enthusiast, a student or just curious about the digital world, this quiz offers an engaging way to challenge yourself. Get ready to tackle a series of thought-provoking questions designed to cover a wide spectrum of computer-related topics. From the core components that power these machines to the programming languages that bring them to life, our quiz will put your understanding to the test. Prepare for a fun and enlightening experience that celebrates the ever-evolving world of computers.
Directions: In the questions given below, four options have been given. Click on the option which you think is the RIGHT ANSWER to the question.
Score 0
| Question |
|---|
|
1. A computer virus normally attaches itself to another computer programme known as a |
|
2. One byte consists of - |
|
3. The amount of time required by a storage device to retrieve data and programmes is its |
|
4. ENIAC was |
|
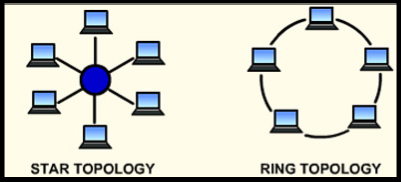
5. Which of these describes attempts by individuals to obtain confidential information from a computer user by falsifying their identity? |
|
|
6. The first computer made available for commercial use was - |
|
7. A person who uses his or her expertise to gain access to other people's computers to get information illegally or do damage can be called a |
|
8. A 32-bit word computer can access _____ bytes at a time. |
|
9. The process of transferring files from the Internet to your computer is called - |
|
10. The ____ shows all the web sites any pages that you have visited one a period of time. |
|
11. The language which provides basic building blocks for web pages is known as - |
|
12. In the URL, http//:www.leadthecompetition.in, the portion labelled http is the ____ |

|
|
13. Which of the following is a read only memory storage device? |
|
14. A repair for a known software bug usually available at no charge on the internet is called a |
|
15. Which of the following connects the computer to a telephone line? |
|
16. What is an e-mail attachment? |
|
17. If a file has a '.bak' extension it refers usually to - |
|
18. The window which shows icons for things like the mouse, sound, and display is called |
|
19. What kind of file has an extension '.mpg'? |
|
20. Which of the following is not real security and privacy risks? |
|
21. Which of the following defines the ability to recover and read deleted or damaged files from a criminal’s computer? |
|
22. The difference between people with internet access and those without it is known as the - |
|
23. The smallest unit in a digital system is a |
|
24. Which of the following is a web browser? |
|
25. Junk e-mail is also called ____ |
|
26. Who of the following is the founder of Facebook? |
|
27. In which of the following areas, spreadsheet software is more useful? |
| Question | |
|---|---|
|
28. What is windows explorer? | |
|
29. Which of the following terms refers to unwanted and unsolicited e-mails received by us? | |
|
30. A Groupware is a - | |

| |
|
31. A DVD is An example of a/an | |
|
32. A word in a web page that, when clicked opens another document is called - | |
|
33. Which of the following is the most commonly used operating system? | |
|
34. Windows 7, the operating system from Microsoft Corporation has ________ Indian languages fonts. | |
|
35. A megabyte is actually equal to ______ kilobytes | |
|
36. Which of the following launched the AI chatbot named ChatGPT? | |
|
37. Which of the following was referred to as a 'three-finger salute' by Microsoft founder Mr. Bill Gates? | |

| |
|
38. What is the full form of GUI? | |
|
39. Which command allows you to reduce fragments of file and optimize the performance of disk? | |
|
40. A communication processor that connects dissimilar networks by providing the translation from one set of protocol to another is - | |
|
41. What is a fraudulent practice of extracting details of someone's bank card or account illegally via phone known as? | |
|
42. In a Database Management System (DBMS), the content and the location of the data is defined by the - | |
|
43. Which of the following is the ascending order of data hierarchy? | |
| |
|
44. A Computer executes Programs in the sequence of: | |
|
45. The part of a computer system containing the circuitry that does the adding, subtracting, multiplying, dividing and comparing is called as - | |
|
46. In terms of networking what does VPN stand for? | |
|
47. Which of the following was the earliest to be developed? | |
|
48. Which of the following is commonly used for undoing the previous action in a computer application? | |
|
49. Which language was used to communicate with the earliest computers? | |
|
50. In which year did Microsoft release the first version of Windows | |
|
51. Who was the creator of the World Wide Web? | |
|
52. Which of the following was the first widely available computer game? | |
|
53. Which of the following was the first search engine? | |
|
54. Which of the following programming languages has been developed by Microsoft? | |
|
55. What is the term used for a fault or error in the development and operation of a program? | |